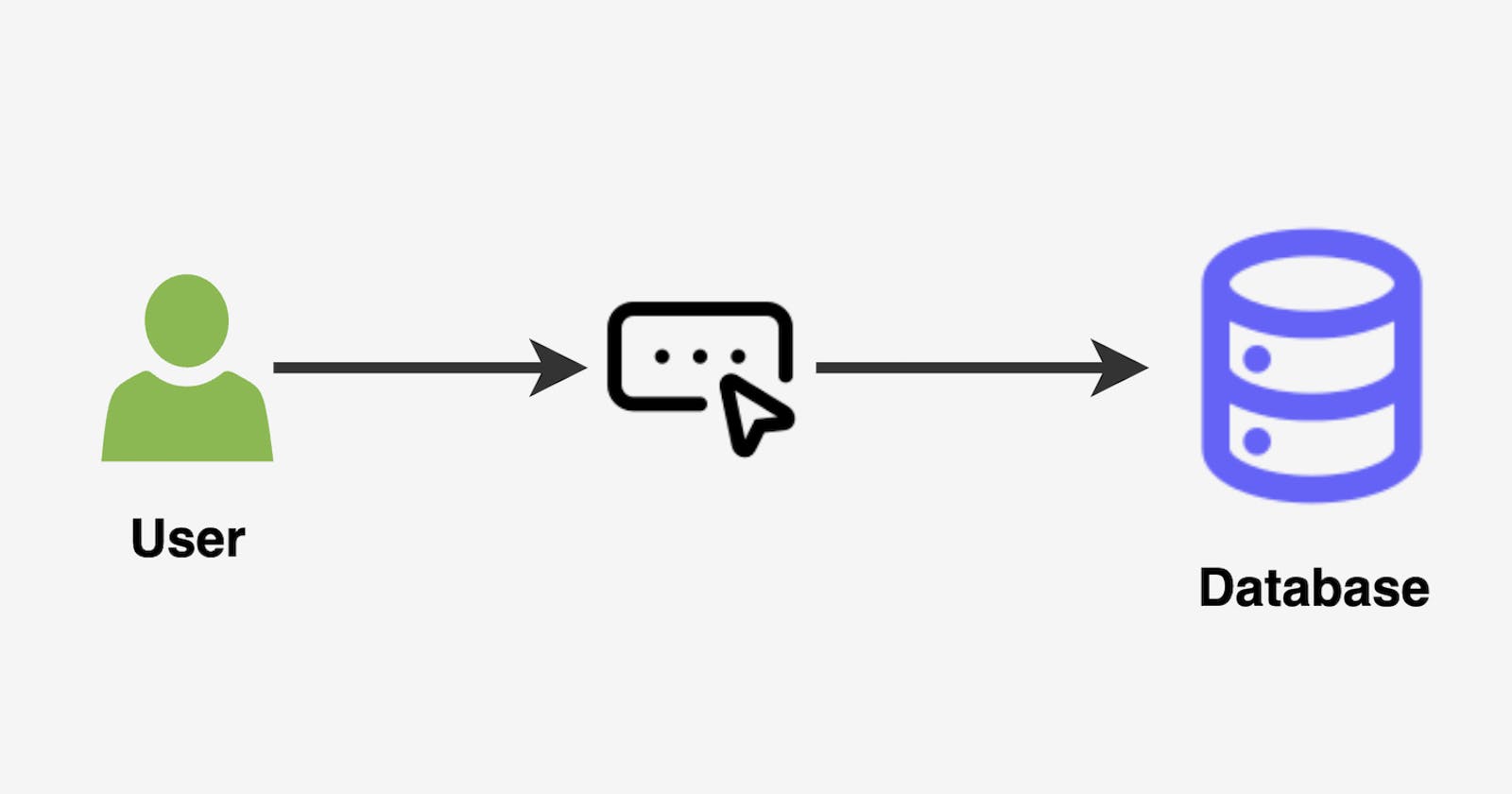
Authentication is a vital aspect of any service. Experienced developers understand the importance and complexity of implementing a robust authentication strategy. Even a small error in authentication can result in a data breach and damage to the reputation of the service.
Before we continue if you are confused between Authentication and Authorization you can out this article:
Most services today use username and password combinations to authenticate their users. These credentials must be stored securely, typically in a database. In this article, we will discuss “How to store these credentials in a database” to ensure their security and use them for user authentication.
Let’s discuss this!
Ways of Storing Credentials:
There are many ways to store login credentials. Here are a few of them:
Plaintext Storage: This method involves storing the login credentials in a plain, unencrypted form. This is not a secure option because anyone with access to the database could view the login credentials.
Encryption: This method involves using an encryption algorithm to transform the login credentials into a secure, encrypted form. The encrypted credentials are stored in the database, and a separate key is required to decrypt them. This is a very secure option, but it requires the use of a secure key management system.
Hashing: This method involves using a one-way hash function to transform the password into a fixed-length string of characters. The hashed password is stored in the database, and the original password is not kept. This is a more secure option than plaintext storage.
Since Plaintext storage is not an option that leaves us with either encryption or hashing.
Encryption Vs Hashing:
Encryption is a process that uses a secret key to transform a password into a secure, encrypted form. When a user wants to log in, the encrypted password is decrypted using the same secret key and compared to the entered password to determine if it is valid. If a hacker were to gain access to the secret key, they could potentially use it to decrypt and access all of the encrypted passwords, making it important to keep the secret key secure.
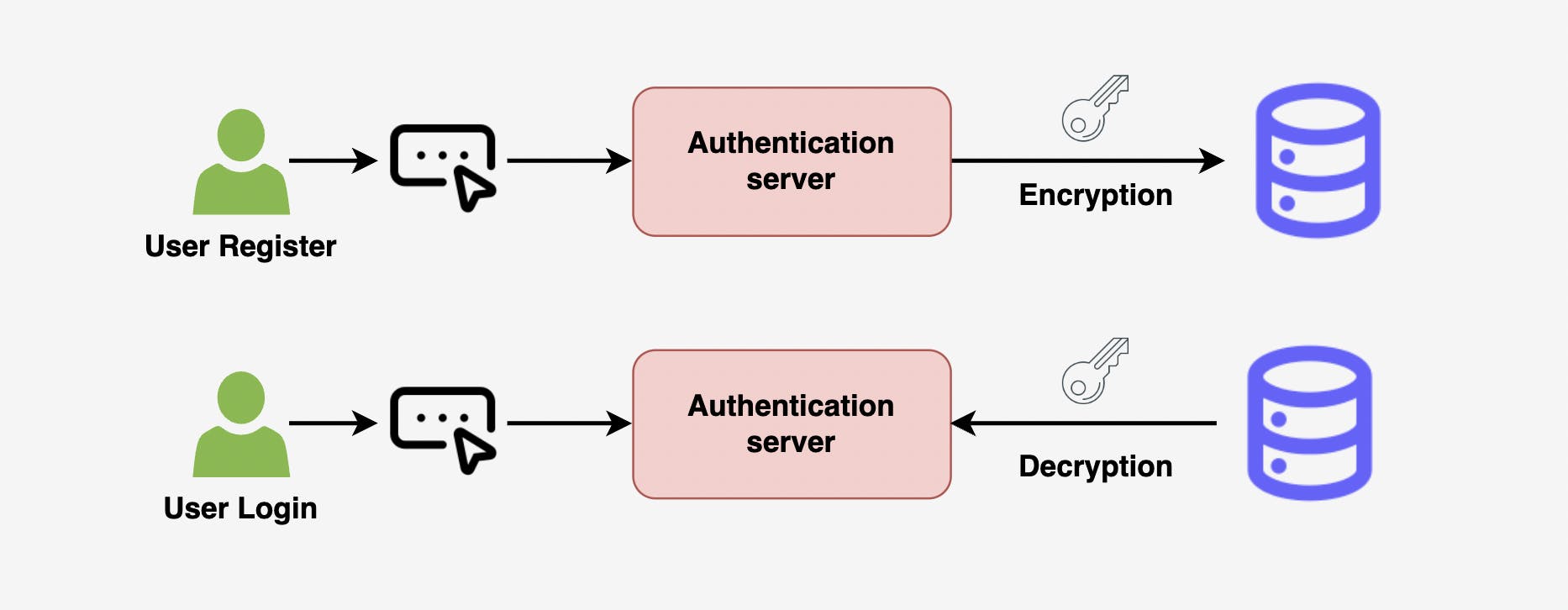
Hashing is a one-way cryptographic function that converts a password into a fixed-size hash value. One of the benefits of hashing is that it always produces the same hash value for a given password, making it possible to directly compare the hash value stored in a database to the hash value of a password entered by a user. Additionally, because hashing is a one-way function, it is not possible to reverse the process and retrieve the original password from the hash value, adding an additional layer of security.
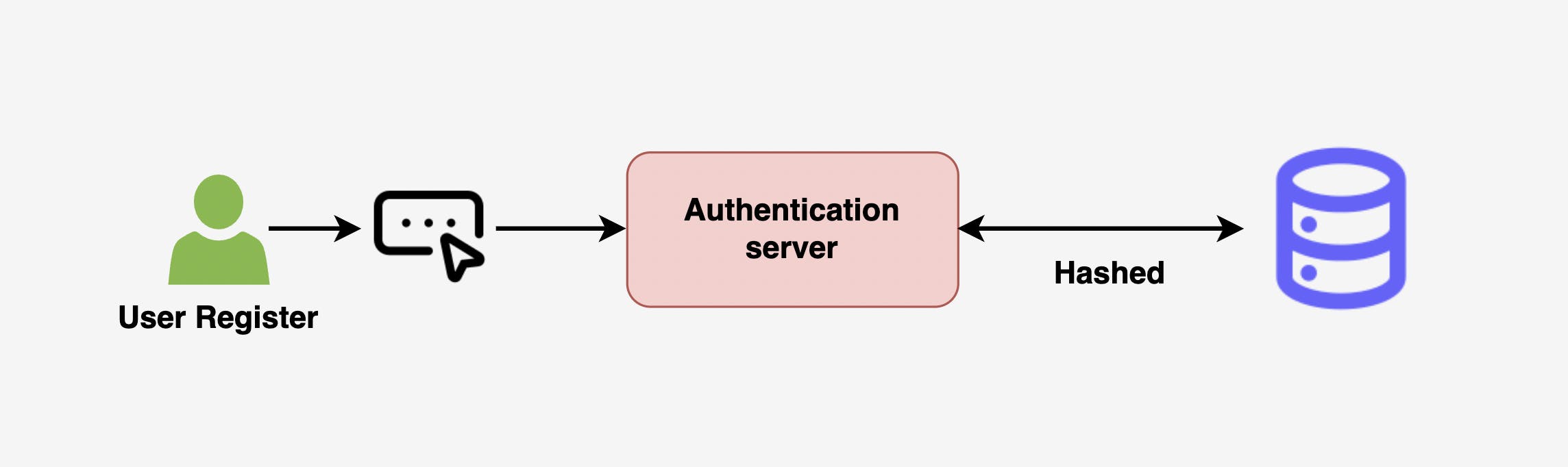
Does that mean hashing is the most secure option?
Well not exactly, While hashing is a more secure method for storing passwords than encryption, it is not foolproof. Hackers can use precomputed hash tables, known as rainbow tables, to crack hashed passwords. Rainbow Tables contain a list of commonly used words and their corresponding hash values, making it easier for hackers to crack simple or weak passwords. It is important to use strong, unique passwords to make it more difficult for hackers to crack them using rainbow tables or other methods.
So, even hashing is not a secure option. Is there actually a way to securely store passwords?
Adding Salt And Pepper
Not actually :)
Salting
Salt is a unique, random string that is generated and added to the password before it is hashed. Storing the salt value along with the hashed password allows the salt to be used to recreate the hash value when a user logs in and enters their password.
Formula: Hash(Unique Salt + Password)
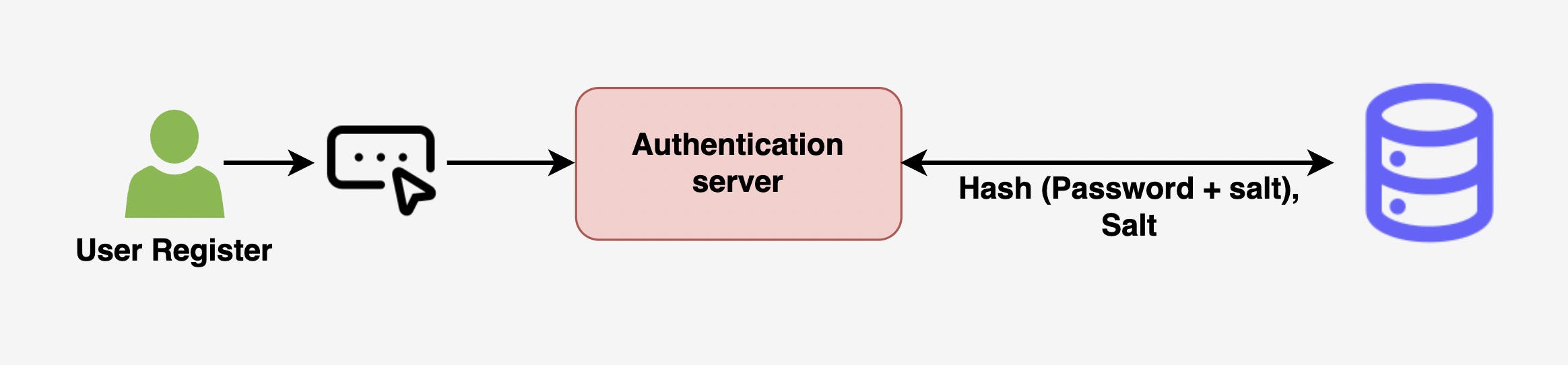
There are several benefits to using salt when hashing passwords:
If multiple users have the same password, their hash values will still be different due to the unique salt values that are added to the passwords before they are hashed.
The combination of the password and the salt increases the length of the string that is hashed, making it more difficult for hackers to use rainbow tables or other precomputed hash tables to crack the passwords.
By adding a unique salt value to each password, it becomes more difficult for hackers to use precomputed hash tables to crack multiple passwords at once.
Pepper
Pepper is a common secret added to the “Password + Salt” combination before hashing. Pepper is common to all passwords and stored at the service layer or in a different location other than the hash and salt database.
Formula: Hash(Unique Salt + Password + Common Pepper)
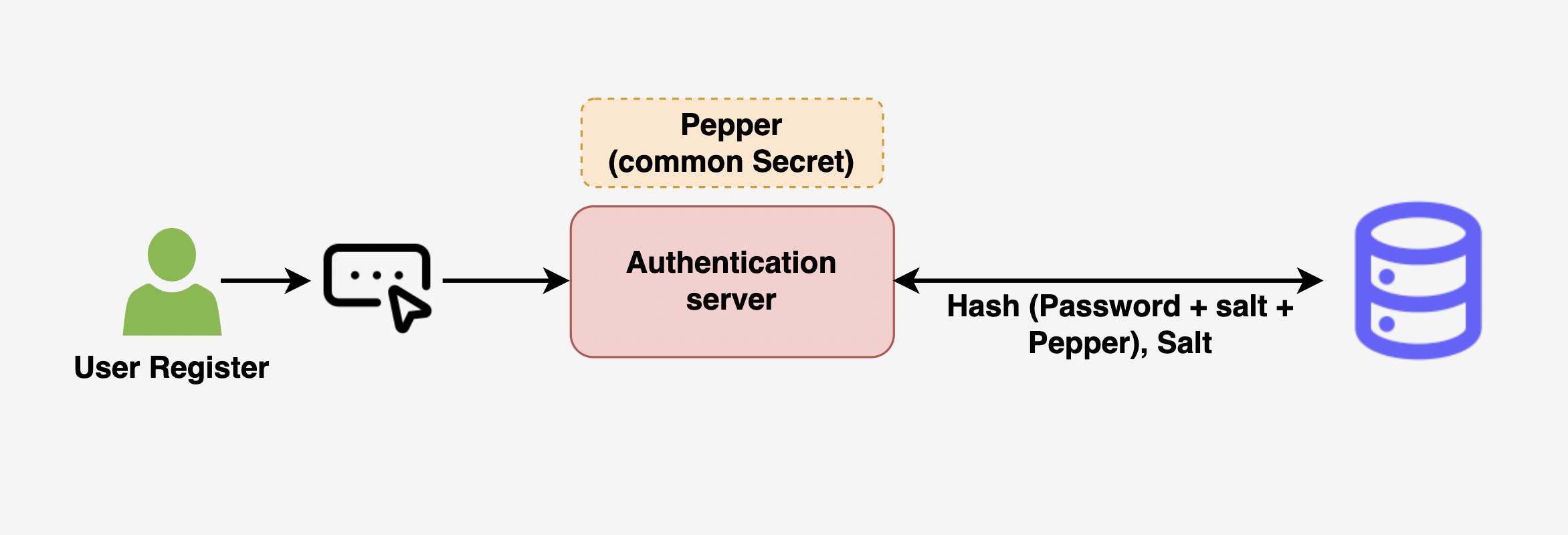
The benefit of pepper is if the hash and salt database is compromised, passwords are not compromised. Since, the pepper part of the formula is not available, as it is stored on a different server.
The combination of Password, Salt, and Pepper is a secure way to store login credentials.
Log Credential Table
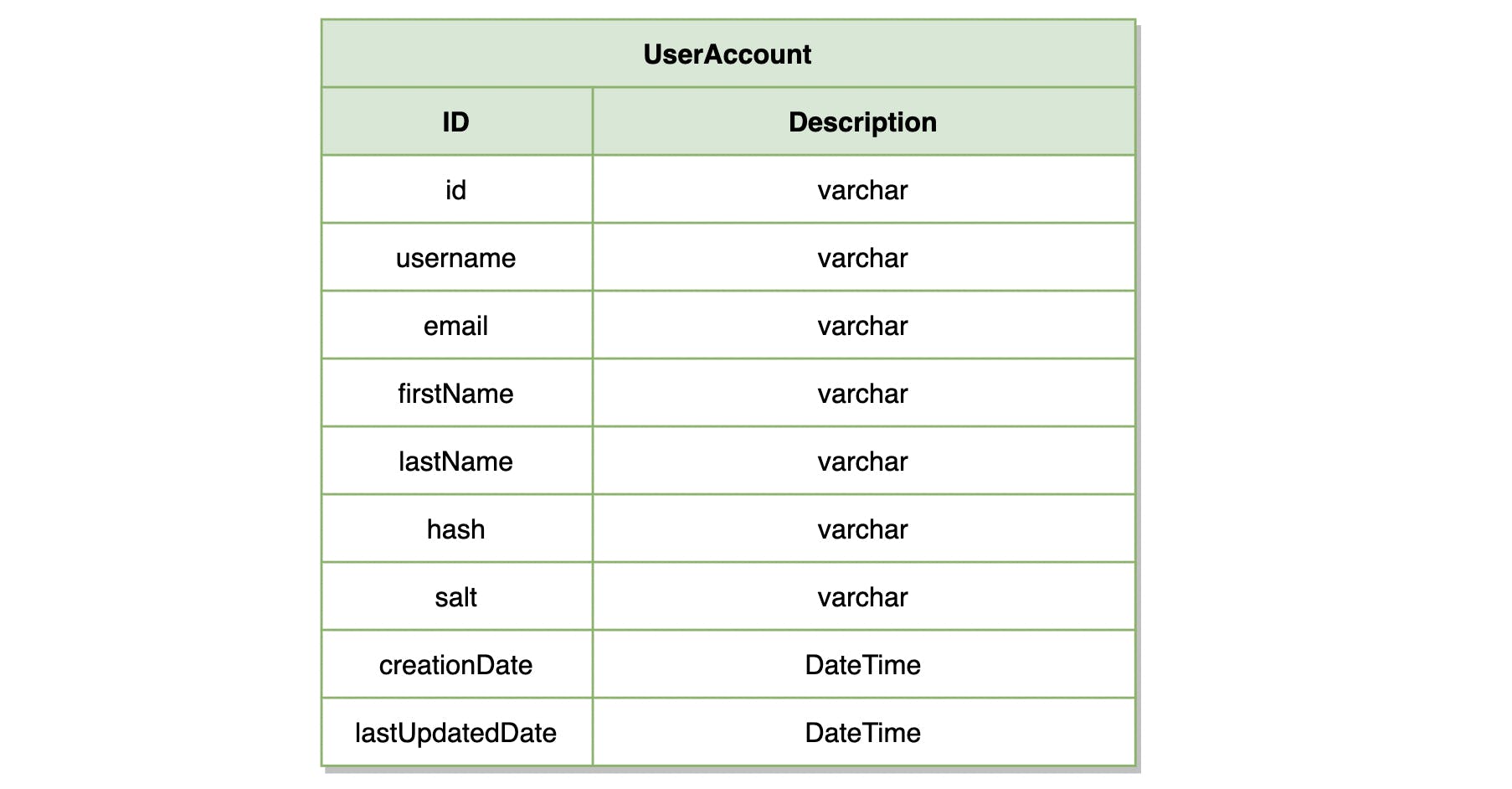
id: An auto-generated ID.username: Unique string used to login into the system. It can be a username, an email, or even a phone number.firstName: The user’s first name.lastName: The user’s last name.email: The user’s email address. This is used to confirm account creation or send password reset confirmations.hash: A hash string for the user’s password plus the salt and pepper combination.salt: A unique, randomly-generated string that is concatenated with the user’s password before it is hashed and stored in theHashcolumn.creationDate: Creation date of the account.lastUpdatedDate: Last updation date for the user account.
Hashing Algorithms
Some common hashing functions include:
MD5 (Message Digest 5): This is a widely used hashing algorithm that produces a 128-bit hash value. While it is relatively fast and has been widely used in the past, it has shown to be vulnerable to collision attacks, in which two different inputs produce the same hash value. As a result, it is generally considered to be less secure than other available options.
SHA-1 (Secure Hash Algorithm 1): This is a 160-bit hashing algorithm that was developed by the National Security Agency (NSA) as a stronger alternative to MD5. While it has been widely used in the past, it has also been shown to be vulnerable to collision attacks and is no longer considered to be a secure option for most purposes.
SHA-2 (Secure Hash Algorithm 2): This is a family of hashing algorithms that includes several different variations with different hash lengths, including SHA-256 and SHA-512. It was developed by the NSA as an improvement over SHA-1 and is generally considered to be more secure.
SHA-3 (Secure Hash Algorithm 3): Hashing algorithm that was developed as an alternative to SHA-2. It includes several different variations with different hash lengths, including SHA3–256 and SHA3–512. It is designed to be resistant to collision attacks and is considered to be a secure option for most purposes.
BLAKE2: This is a fast, secure hashing algorithm that produces a fixed-size hash value. It is designed to be resistant to collision attacks and is suitable for a wide range of applications.
Argon2: This is a modern, secure hashing algorithm that is designed specifically for password hashing. It was designed to be resistant to attacks using specialized hardware, such as graphics processing units (GPUs), and is considered to be a very secure option for password storage.
Bcrypt: Bcrypt is a password hashing function that is specifically designed to be computationally expensive to perform. It is a secure password hashing function that uses a salt and the Blowfish cipher to make it difficult to crack hashed passwords. It is widely used and considered a good option for password storage.
Each of these algorithms has its own unique characteristics and level of security. It is important to carefully consider the strengths and weaknesses of different hashing algorithms and choose one that is appropriate for your specific needs. It is also a good idea to periodically review and update the hashing algorithm you are using to ensure that it remains secure against current and emerging threats.
That’s all about “How to Store Passwords in a Database”. Send us your feedback using the comment section. Your feedback helps us create better content for you and others. Thanks for reading!
If you like the article please like and share. To show your support!
Thanks.