Authentication and Authorization in Microservices. Every developer should know
While Authentication and Authorization are important in both microservices and monolithic architectures, the decentralized nature of microservices requires additional attention to these security measures in order to protect against potential vulnerabilities and ensure the security, reliability, and integrity of the system.
In this article, we will explore the key concepts of authentication and authorization and how they can be used to protect microservices.
Let’s get started!
First, let’s understand the difference between Authentication and Authorization.
Difference between Authentication and Authorization
Both terms are closely related concepts often used together to secure systems and protect against unauthorized access

Authentication:
The process of verifying a user is who he claims to be. This is usually done via a username and password or using a centralized registry that can identify the user.
Authorization:
The process of verifying if the user has permission to specific resource or action. Once the user is authenticated, the system can use authorization to determine what actions or resources the user is allowed to access.
In summary, authentication is about verifying identity, while authorization is about granting or denying access based on that identity.
Different strategies in a Microservice Architecture:
In a monolithic architecture, the entire system is contained in a single codebase, making it easier to manage user access and permissions. In a microservices architecture, however, user access and permissions must be managed for each individual microservice, which can be more complex.
Here are some of the ways to manage Authentication and Authorization in microservices:
Centralized Authentication and Authorization:
Creating a separate microservice that is responsible for handling all authentication and authorization requests for a system.
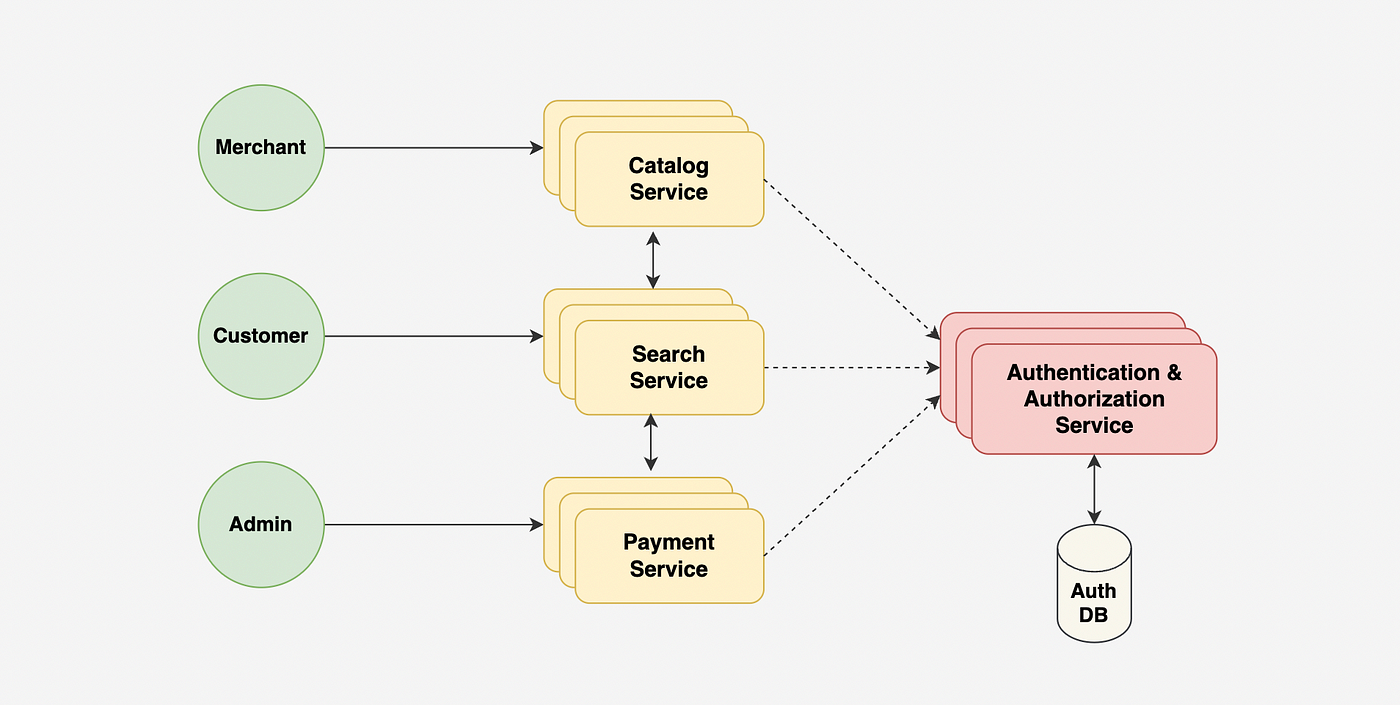
This approach has a few benefits:
Simplicity: Easier to manage user accounts and permissions, as well as to implement and enforce security policies.
Scalability: Can handle a large number of requests and can be easily scaled up or down as needed.
Reusability: Other microservices or applications within the system can leverage the centralized service for authentication and authorization, reducing the need to implement these features separately for each service.
However, there are also some potential drawbacks to using a centralized authentication and authorization service:
Dependency: If the centralized service is unavailable or experiencing issues, it can impact the availability of the entire system.
Vulnerability: A centralized service can be a single point of failure, making it a potential target for attackers.
Complexity: Implementing and maintaining a centralized authentication and authorization service can be more complex than implementing these features directly within each microservice.
The approach will depend on the specific requirements and constraints of your system. It may be a good option for systems with a high volume of authentication and authorization requests.
Distributed Authentication and Authorization:
Distributing the responsibility for authentication and authorization across multiple microservices or components within a system.

This approach can have a few benefits:
Resilience: The system becomes more resilient to failures or outages. If one component fails, other components can still handle authentication and authorization requests.
Performance: Improve the performance of the system, as multiple components can handle requests in parallel rather than relying on a single, centralized service.
Flexibility: Each component can have its own authentication and authorization logic, allowing for more customization and control.
However, there are also some potential drawbacks to using a distributed authentication and authorization approach:
Complexity: Implementing and maintaining distributed authentication and authorization can be more complex than using a centralized service, as there may be more components to manage and coordinate.
Security: Distributed authentication and authorization can also introduce additional security challenges, as there may be more potential attack vectors for attackers to exploit.
The approach will depend on the specific requirements and constraints of your system. It may be a good option for systems that need to be highly resilient and scalable.
Centralized authentication service (API Gateway) and distributed authorization:
Using a centralized service to handle authentication requests, but distributing the responsibility for authorization across microservices or components within the system. This approach combines the benefits of centralized authentication (such as simplicity and scalability) with the benefits of distributed authorization (such as resilience and flexibility).
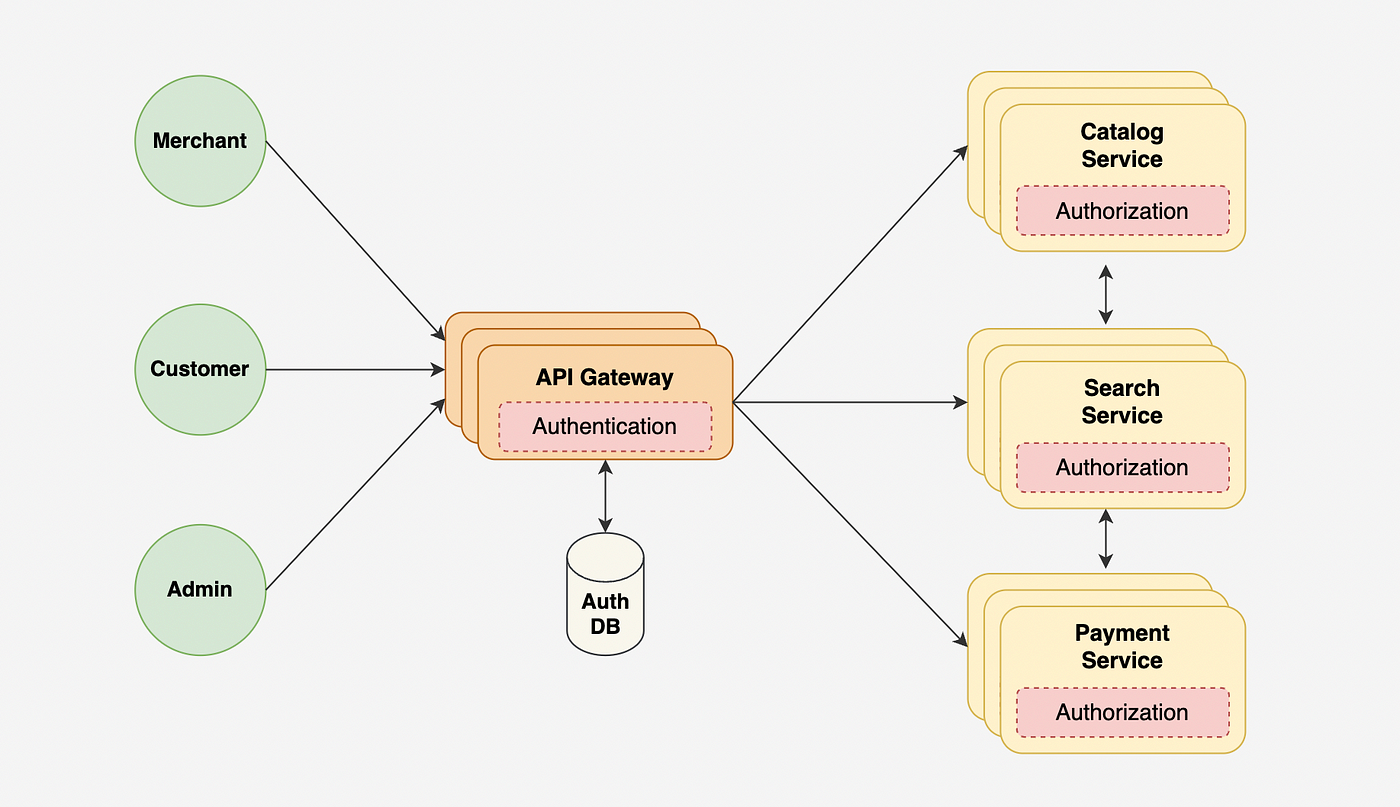
One potential benefit of this approach is that it allows for more efficient and scalable authentication, while still providing the ability to customize and control authorization logic at the individual service level. This can be particularly useful in systems with a high volume of authentication requests, as the centralized authentication service can handle these requests more efficiently than if each service implemented authentication individually.
However, there are also some potential drawbacks to this approach:
Complexity: Implementing and maintaining a centralized authentication service with distributed authorization can be more complex than using a centralized service for both authentication and authorization, as there may be more components to manage and coordinate.
Security: There may also be additional security considerations when using this approach, as the centralized authentication service may be a potential target for attackers.
The approach will depend on the specific requirements and constraints of your system. It may be a good option for systems that need to scale efficiently and provide more flexibility in terms of authorization logic.
Types of Authentication:
There are different types of authentication methods that can be used to verify user identity here are a few of them:
Passwords: A combination of Username (mobile number/email) and password to verify identity. A password is a combination of letters, numbers, and symbols that a user must enter correctly to gain access to a system. However, cause of the increasing number of services that we use it has become difficult to memorize all these usernames and passwords. As a result, users tend to forget or use the same password across services. Cybercriminals use phishing, data breaches, and others to exploit this.
Two-factor authentication: A process that requires a user to provide two different authentication factors, such as a password and a fingerprint, a security token, OTP, Push notification, or others, to access a system.
Security tokens: Physical devices, such as a key fob or a card, that generate a unique code that must be entered along with a password to gain access to a system. Security tokens are often used as an additional layer of security in addition to a password. They provide an extra level of protection because they are physical devices that must be present in order to log in, which makes it more difficult for an attacker to gain access to a system.
Biometric authentication: A process that uses physical characteristics, such as a fingerprint or a facial recognition scan, to identify a user. Biometric authentication is often used as an additional layer of security, in addition to traditional methods such as passwords or security tokens. It can provide a high level of security because it is based on unique physical characteristics that are difficult to forge or imitate.
Certificate-based authentication: A process that uses digital certificates and public key infrastructure (PKI) to verify the identity of a user or device. In this process, a digital certificate is issued by a trusted certificate authority (CA) and contains a public key and the identity of the certificate owner. When a user or device wants to authenticate to a system, they present their digital certificate. The system then uses the public key in the certificate to encrypt a message, which is sent back to the user or device. The user or device decrypts the message using their private key, which only they possess. If the decrypted message is correct, the authentication is successful.
It is also used in secure communication protocols such as HTTPS and SSL/TLS.Single sign-on (SSO): A process that allows a user to use a single set of login credentials to access multiple systems or applications. User only needs to enter their login credentials once, and they will be automatically logged in to all of the systems or applications that they are authorized to access. This can make it more convenient for users because they don’t need to remember multiple sets of login credentials.
Multi-factor authentication: A process that requires a user to provide multiple authentication factors, such as a password, a security token, a fingerprint, OTP, mobile Authenticators, Push notification, and hardware token to access a system. You can choose any of these techniques according to your needs and requirement.
Protocols:
There are many different authentication protocols that can be used to verify the identity of a user or device.
Password Authentication Protocol (PAP): A simple protocol that transmits a username and password in plaintext over the network. PAP is not secure because it does not encrypt the password, so it should not be used in most cases.
Challenge Handshake Authentication Protocol (CHAP): A protocol that uses a three-way handshake to authenticate a user. The protocol reauthenticate periodically even within the same session. CHAP does not transmit the password over the network, which makes it more secure than PAP.
Extensible Authentication Protocol (EAP): A flexible framework that allows different authentication methods to be used over the same network. EAP is often used in wireless networks and VPNs.
Kerberos: A network authentication protocol that uses secret-key cryptography to secure communications between clients and servers.
Remote Authentication Dial-In User Service (RADIUS): A protocol that allows a central server to authenticate users on multiple network devices. RADIUS is often used in combination with other authentication protocols, such as PAP or CHAP.
Lightweight Directory Access Protocol (LDAP): Lightweight directory access protocol (LDAP) is a protocol that makes it possible for applications to query user information rapidly. The protocol allows users to access directory services over a network. LDAP can be used for authentication, as well as for storing and retrieving user information.
Security Assertion Markup Language (SAML): This is an XML-based protocol authentication that exchanges data between Identity Providers (IdPs) and Service Providers. SAML makes Single Sign On possible by authenticating a user and then communicating the User identity to other applications.
Open Authorization or OAuth 2.0: OAuth 2.0 is a widely used authorization technique that allows users to grant third-party applications access to their resources without sharing their login credentials. It works by allowing the user to authenticate directly with the site holding their resources, and then granting the third-party application permission to access those resources through the use of an access token. OAuth 2.0 is used by many popular websites and applications like Facebook, Google, Twitter, etc, and it helps to protect users’ login credentials while providing a secure and convenient way for them to grant access to their resources.
In summary, authentication and authorization are crucial for protecting microservices-based systems and ensuring the security, reliability, and integrity of the system as a whole.
That’s all about Authentication and Authorization in Microservices. Send us your feedback using the message button below. Your feedback helps us create better content for you and others. Thanks for reading!
If you like the article please like and share. To show your support!
Thanks.